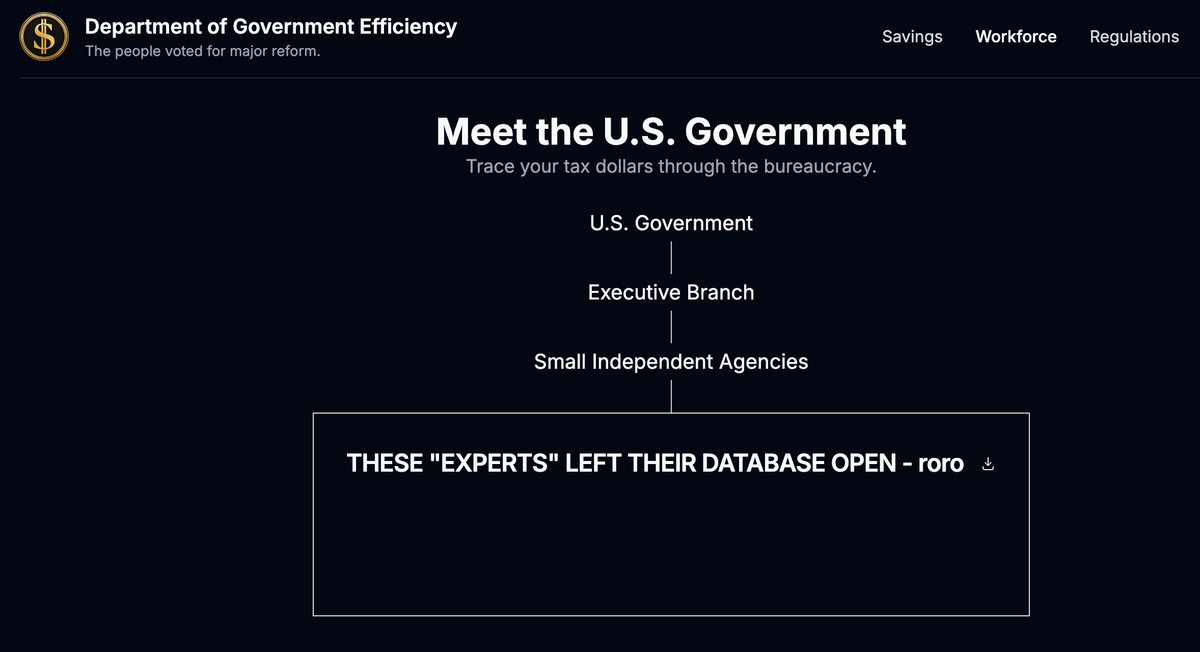
"One coder added at least two database entries that are visible on the live site and say “this is a joke of a .gov site” and “THESE ‘EXPERTS’ LEFT THEIR DATABASE OPEN -roro.” "
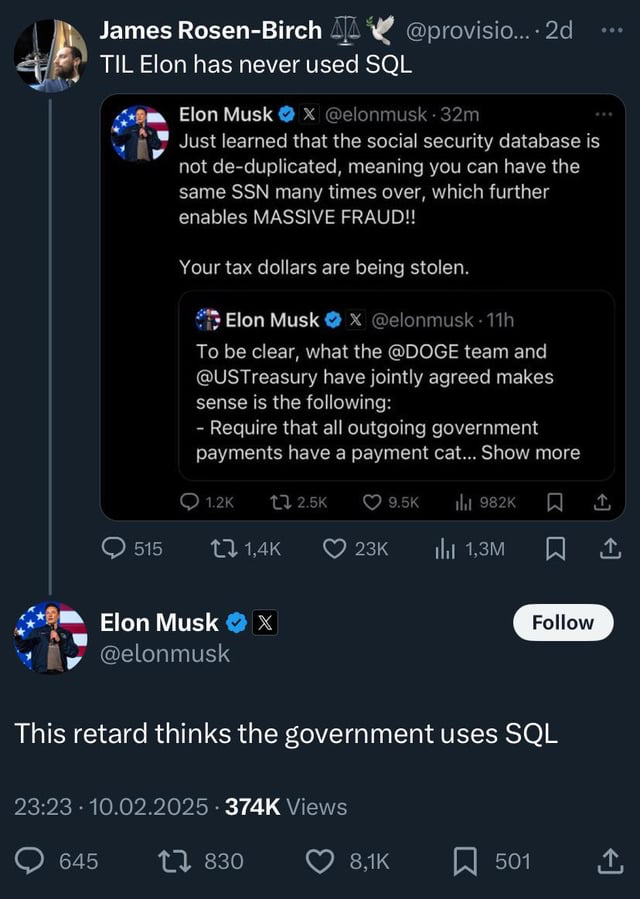
Techbros are incompetent?! Who knew.
Can’t move fast and break things with things that aren’t broken.

Competent employees are expensive and don’t support the administration’s goals.
Oooh that’s juicy. I wonder how many holes they left in the important production systems that they’ve been touching.
I also wonder, with how progressive and dissenting American programmers and cybersec experts are, if our l33t h4x0r sk1llz could be turned against DOGE?
Not suggesting anything wildly destructive, just some friendly grey-hat trolling to slow them down and expose their flaws. Think of it as a complimentary pen-test.
Part of me also thinks they are hoping some people will slip in some “proof” of fraud somewhere, like how people “proved” the COVID vaccine was killing people via VAERS.
Yes. But how?
Here’s an archived version of the article to get past the paywall. The hackers went to the network tab of their browser’s developer console and noticed that the API calls to write to the database weren’t password protected.
Compared with an SQL injection, how sophisticated is this method?
If SQL injection is picking a lock, this is entering through an unlocked door.
Not sophisticated at all, authentication on API routes is way earlier on the security checklist than SQL query sanitisation. This site is amateur work.
Much much simpler, with a SQL injection at least you have to bypass the filters set, this is just submitting the changes through an API and the DB just eats it up.
Not to worry, they don’t use SQL